WordPress Security: Brute Force Amplification Attack
Most of the times, we have reported about WordPress vulnerabilities involving vulnerable plugins, but this time security researchers have discovered Brute Force Amplification attacks on the most popular CMS (content management system) platform.
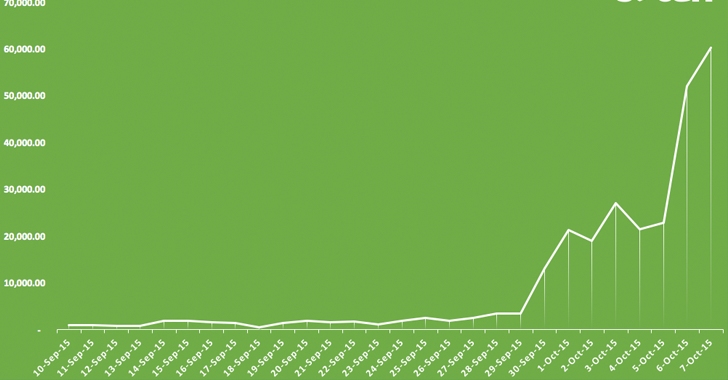
Researchers from security firm Sucuri have found a way to perform Brute Force amplification attacks against WordPress’ built-in XML-RPC feature to crack down administrator credentials.
XML-RPC is one of the simplest protocols for securely exchanging data between computers across the Internet. It uses the system.multicall method that allows an application to execute multiple commands within one HTTP request. A number of CMS including WordPress and Drupal support XML-RPC.
But…
The same method has been abused to amplify their Brute Force attacks many times over by attempting hundreds of passwords within just one HTTP request, without been detected.
Amplified Brute-Force Attacks
- Go undetected by normal brute-force mitigation products
- Try hundreds of thousands of username and password combinations with few XML-RPC requests.
“With only 3 or 4 HTTP requests, the attackers could try thousands of passwords, bypassing security tools that are designed to look and block brute force attempts,” Sucuri’s researchers wrote in a blog post.